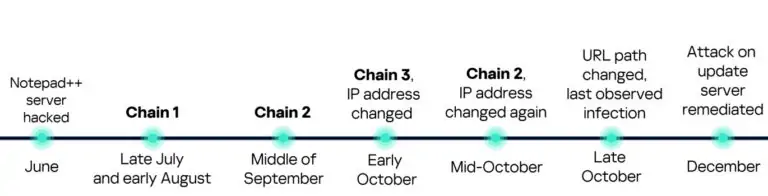
Microsoft Shares Third Edition of Cyber Signals, Highlights New Security Risks for IT Teams
Internet-of-Things (IoT) and Operational Technology (OT) device pervasiveness, susceptibility, and cloud connectivity provide a fast-rising, frequently unregulated risk surface affecting a broader range of industries and organizations.
The rapid growth of IoT provides attackers with a larger entry point and attack surface. Access to less secure OT is creating the possibility for devastating infrastructure attacks as OT becomes more cloud-connected and the IT-OT gap closes.
Threat briefing
Adversaries compromise internet-connected devices to gain access to sensitive critical infrastructure networks.
Microsoft has noticed threats abusing devices in practically every monitored and visible area of an enterprise during the last year. These vulnerabilities have been observed in traditional IT equipment, OT controllers, and IoT devices like as routers and cameras.
The increased presence of attackers in these contexts and networks is being spurred by the convergence and interconnection that many enterprises have adopted in recent years.
According to International Data Corporation (IDC), there will be 41.6 billion linked IoT devices by 2025, representing a faster growth rate than traditional IT equipment. Although IT equipment security has improved in recent years, IoT and OT device security has lagged, and threat actors are leveraging these devices.
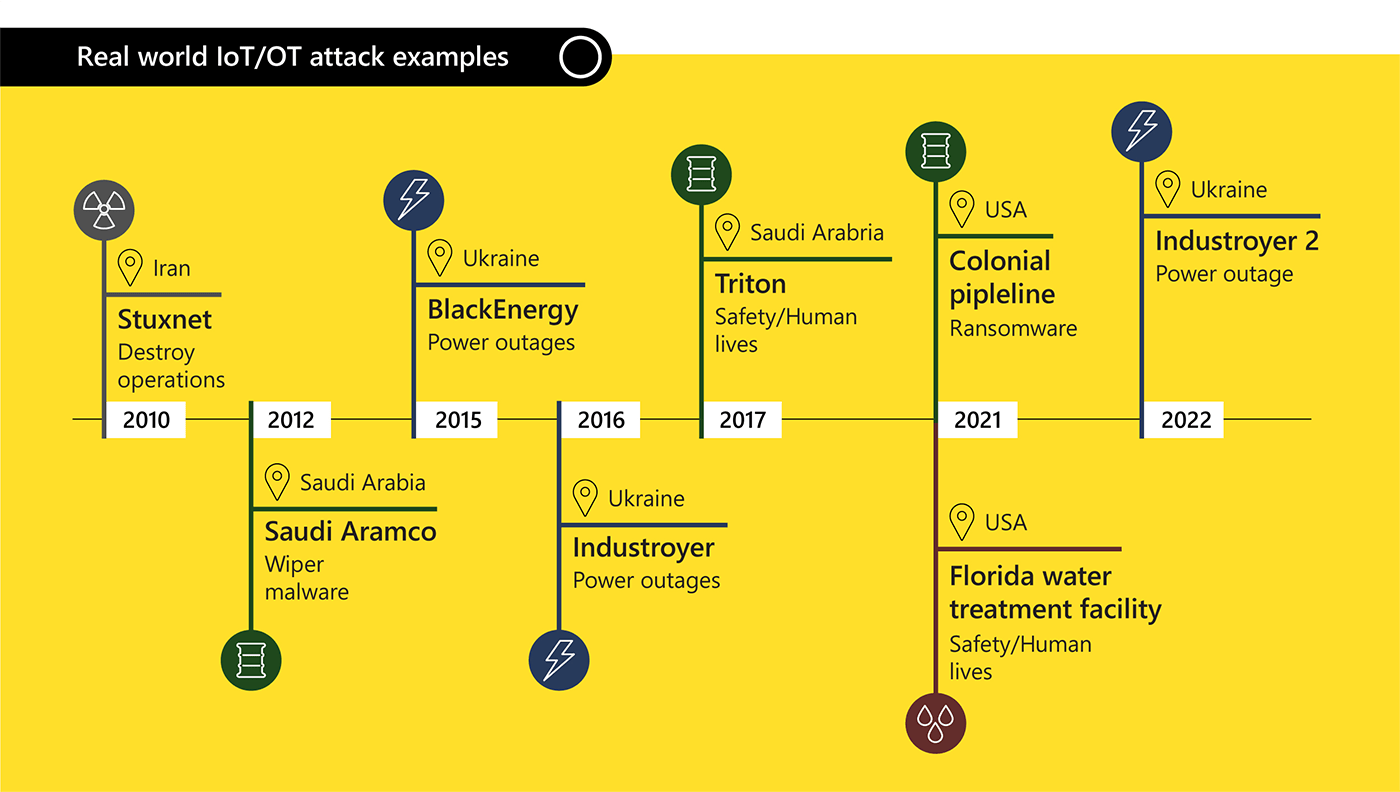
It is crucial to realize that attackers may have a variety of motivations for compromising devices other than standard computers and cellphones. Russia’s cyberattacks on Ukraine, as well as other nation-state-sponsored cybercriminal behavior, show that certain nation-states regard cyberattacks on key infrastructure as desirable for attaining military and economic goals.
Seventy-two percent of the software exploits used by “Incontroller,” a revolutionary collection of state-sponsored, industrial control system (ICS) centered hacking tools described by the Cybersecurity and Infrastructure Security Agency (CISA), are now available online. As skill and other barriers to entry disappear, such proliferation encourages larger attack action by other parties.
Threat actors have more options for waging large-scale attacks as the cybercriminal economy grows and malicious software targeting OT systems becomes more widespread and easier to employ. Ransomware attacks, previously thought to be an IT-focused attack vector, are now affecting OT environments, as seen in the Colonial Pipeline attack, which temporarily shut down OT systems and pipeline operations while incident responders worked to identify and contain the spread of ransomware on the company’s IT network. Adversaries realize that the financial impact and extortion leverage of shutting down energy and other critical infrastructures is far greater than other industries.
OT systems encompass practically everything that supports physical operations and cover dozens of vertical industries. OT systems aren’t just for industrial processes; they can also be for any special-purpose or computerized equipment, such as HVAC controllers, elevators, and traffic signals. OT systems include a wide range of safety systems.
Microsoft has noticed Chinese-linked threat actors targeting vulnerable home and small office routers in order to compromise these devices as footholds, providing them with new address space that is less related with their prior operations from which to launch new assaults.
While IoT and OT vulnerabilities provide a concern for all enterprises, critical infrastructure is especially vulnerable. Disabling vital services, rather than deleting them, is a potent tool.
Recommendations:
- Work with stakeholders:?Map business-critical assets, in IT and OT environments.
- Device visibility:?Identify what IoT and OT devices are critical assets by themselves, and which are associated with other critical assets.
- Perform a risk analysis on critical assets:?Focus on the business impact of different attack scenarios as suggested by?MITRE.
- Define a strategy:?Address the risks identified, driving priority from business impact.
Protecting against attackers
IoT opens up new business options while also posing significant risks.
As IT and OT merge to serve growing business needs, risk assessment and developing a more secure link between IT and OT necessitate the consideration of many control mechanisms. Air-gapped devices and perimeter security are no longer adequate for dealing with and defending against new threats like as sophisticated malware, targeted attacks, and malevolent insiders. For example, the rise of IoT malware risks indicates the landscape’s development and ability to overwhelm weak systems.
Microsoft researchers discovered that the highest share of IoT malware, 38 percent of the total, originated from China’s enormous network footprint, after analyzing threat data from 2022 across several countries. With 18% of reported malware spread, infected servers in the United States place the country second.
In OT contexts, advanced attackers employ a variety of strategies and approaches. Many of these tactics are ubiquitous in IT environments but more effective in OT contexts, such as the identification of exposed, Internet-facing systems, the exploitation of employee login credentials, or the exploitation of network access granted to third-party suppliers and contractors.
The confluence of the IT world’s laptops, web apps, and hybrid workspaces and the OT world’s factory and facility-bound control systems poses serious risks by allowing attackers to “jump” air gaps between formerly physically isolated systems. As a result, IoT gadgets such as cameras and smart conference rooms act as risk catalysts by providing innovative entry points into workspaces and other IT systems.
In 2022, Microsoft aided a big multinational food and beverage industry with a virus incident when they were utilizing relatively ancient operating systems to control factory operations. Malware propagated to factory systems via a hacked contractor laptop while performing routine repair on equipment that would later connect to the Internet.
Top countries originating IoT malware infection during 2022
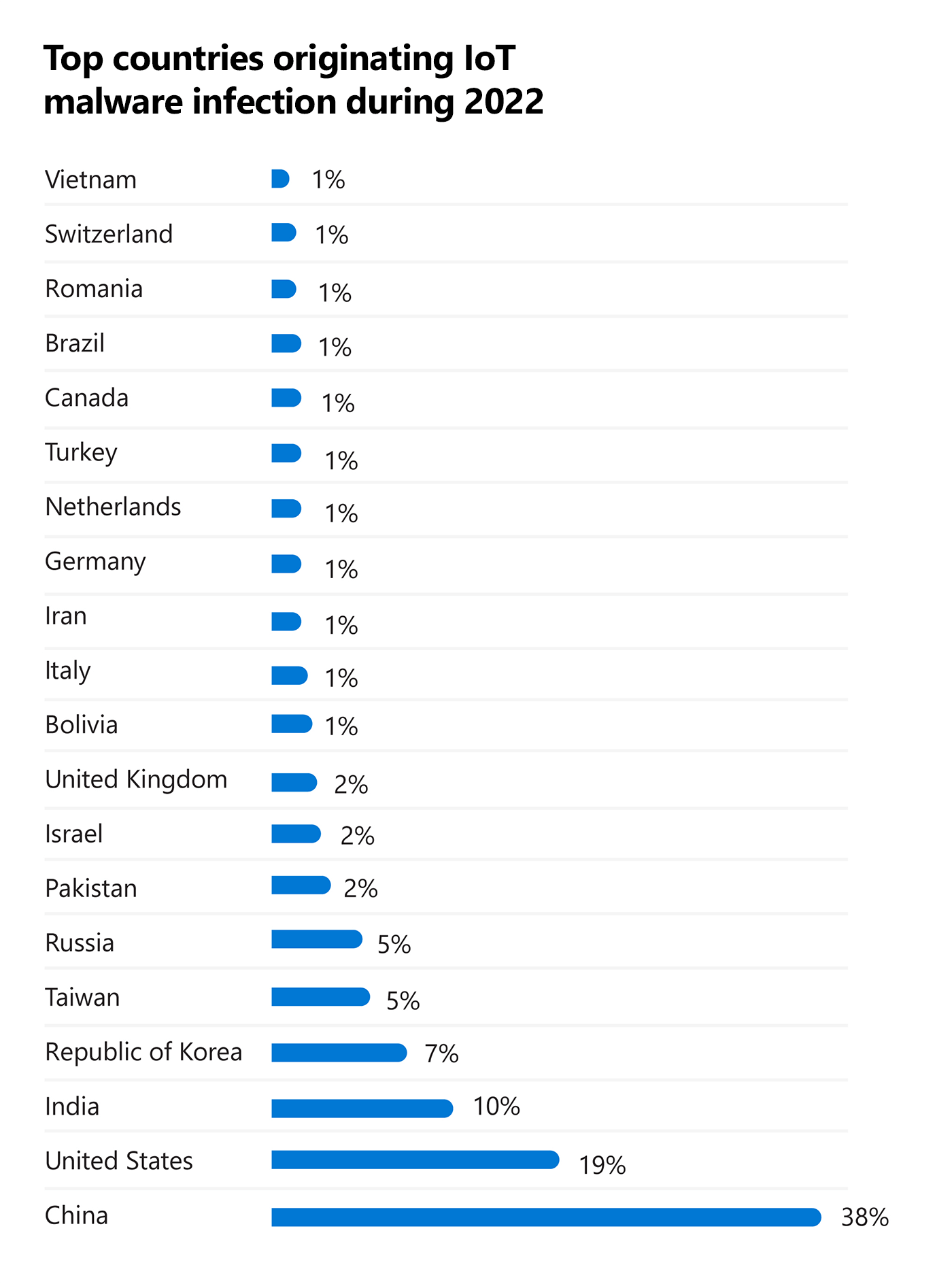
Microsoft threat analysis of 2022 data.
Unfortunately, this is becoming increasingly widespread. While an ICS environment can be air-gapped and separated from the Internet, a compromised laptop becomes susceptible the moment it connects to a previously protected OT device or network. In the customer networks that Microsoft monitors, 29 percent of Windows operating systems are no longer supported. Versions of Windows XP and Windows 2000 have been observed functioning in insecure situations.
Because older operating systems frequently do not receive the necessary updates to keep networks secure, and patching is difficult in large enterprises or manufacturing facilities, prioritizing IT, OT, and IoT device visibility is an important first step in managing vulnerabilities and securing these environments.
In cloud-connected environments, a defense built on Zero Trust, strong policy enforcement, and continuous monitoring can help restrict the potential explosion radius and prevent or control occurrences like these.
Investigating OT equipment necessitates specialized knowledge, and assessing the situation of industrial controller security is critical. Microsoft has made an opensource forensics tool available to the defence community in order to assist incident responders and security specialists in better understanding their surroundings and investigating potential events.
While most people think of key infrastructure as roads and bridges, public transportation, airports, and water and electricity grids, CISA has recommended that space and the bioeconomy be included to the list. Citing the possibility of disruption in numerous sectors of the US economy having a crippling influence on society. Given the world’s reliance on satellite enabled capabilities, cyberthreats in these sectors could have global implications well beyond what we’ve seen thus far.
Recommendations:
- Implement new and improved policies:?Policies stemming from the Zero Trust methodology and best practices provide a holistic approach for enabling seamless security and governance across all your devices.
- Adopt a comprehensive and dedicated security solution:?Enable visibility, continuous monitoring, attack surface assessment, threat detection, and response.
- Educate and train:?Security teams require training specific to threats originating from or targeting IoT/OT systems.
- Examine means of augmenting existing security operations:?Address IoT and OT security concerns to achieve a unified IT and OT/IoT SOC across all environments.
Learn more about how to help protect your organization with insights from David Atch, Microsoft Threat Intelligence, Head of IoT/OT Security Research.
A glimpse of security
From 2020 to 2022, there was a 78% increase in the revelation of high-severity vulnerabilities in popular vendors’ industrial control equipment.1
Unpatched, high-severity vulnerabilities were discovered in 75% of the most prevalent industrial controllers in customer OT networks.1
Over 1 million publicly accessible connected devices on the Internet are using Boa, an obsolete and unsupported software that is still commonly used in IoT devices and software development kits (SDKs).