Don’t Let Yourself or Your Enterprise Get Kidnapped Online!
Picture illustration:blogs.technet.microsoft.com
Cybercrime rates are at an all-time high in Nigeria and world over. Our threat landscape continues to expand. One of the reasons is probably the same as that for the high incidence of traffic accidents on our roads i.e. the widespread belief that- ‘it can’t happen to me’. There is no doubt that awareness levels are extremely low concerning cybercrime but not so much amongst those who are more at risk of being targeted. People who store, transmit and regularly use valuable data be it individuals, corporate bodies or government.
Today, kidnapping has moved online. If you deal with precious data or have some valuable material on your device such as family photographs, financial details, academic documents, enterprise related files or anything that will cause you some anguish should you lose it, then it is important that you read this write up.
This, of course, is not the sort of kidnapping that you are familiar with. I am not even certain it should be termed as kidnapping. There is no physical violence, your person is not threatened and nobody is spirited away to an unknown location pending payment of ransom. However, money is involved, demands are made and something is held to ransom. That is your precious data. This is called Ransomware!
Worldwide, a great multitude of devices have, over the past few years, been locked or had their files encrypted (to conceal data by converting it into a secret code) by tech baddies using malicious programs/software with the purpose of extorting money from the owners of the device or data. You or your enterprise just might be the next victim. Ransomware is a fast growing item of cybercrime as a business. This is because a successful attack generally translates into cash easier and faster than many other forms of cybercrime.
Before now, bad actors would have to ‘steal’ your valuable data and seek out ways to sell it to make some money. This time around, your data is ‘kidnapped’ and sold back to you. The attacker will therefore not need to take the risk of sourcing for a trustworthy buyer for the ‘stolen’ data. He is on the streets in no time having a good time with your money and without any real fears of being accosted by law enforcement.
Though it is unlikely that the attacker will soon be caught because ransomware attacks remain generally untraceable, it is important that you immediately report any incident to the law enforcement agencies. This is because every time an incident is reported, law enforcement agencies and cybersecurity professionals gain better insights and deeper understanding of the problem with a view to finding solutions.
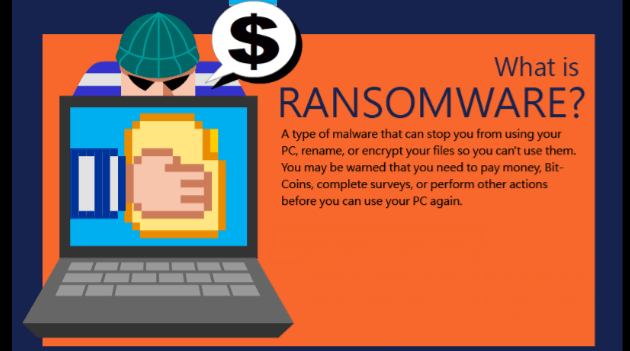
What is Ransomware?
It is simply malware (malicious software) that takes over your device by preventing you from accessing it or accessing the data contents. You are then directed to make payment of a specified sum (ransom) if you wish to regain control of the device. Failing this, the data content of the device would be destroyed and rendered irretrievable. Ransomware is not entirely new but its incidence has increased greatly in the last year or two with attacks becoming more precise, sophisticated and high level worldwide taking government agencies, corporate bodies and individuals as hapless hostages.
More recently however, rather than block/deny you access to your computer or files (lock screen ransomware) attackers will encrypt (encryption ransomware) your files with extremely strong encryption tools and then demand ransom to decrypt said files. The demand is made by a display on your screen giving you directives as to how to make payment and regain access. Variants of Ransomware are CryptoLocker, CryptoWall, TorrentLocker and a host of others all with slightly different modes of causing you great pain. You don’t need to bother yourself with these details though. Let’s leave that stuff for the techie good guys.
Criminals will almost always seek out small and medium sized businesses for a ransomware attack. Many such enterprises do bother to deploy proper online security measures in protection of valuable corporate date. Large organizations and individuals are however also popular targets. Most ransomware attacks are aimed at computers running Windows though Android and Mac OS X are also susceptible to attacks.
The Ransom
The ransom sum could be any amount ranging from the equivalent of a few hundred dollars (in most cases) to many thousands of dollars. It all depends on who you are financially and to what extent Satan has made a home in the soul of your attacker. However, by demanding small amounts of money, attackers realise that victims are more than willing to pay up rather than waste precious time and resources in a generally futile bid to free up the encrypted data.
In some cases, the attacker restores access to the computer after payment is made. In most cases however, restoration is either impossible or the attacker actually proceeds to destroy the data. This is why most professionals will advise you not to pay the ransom, because there isn’t much of a guarantee that the attacker make the decryption key available. However, if your files are critical to you or your business and time is of great essence, then you may have no alternative than to pay up and pray that the attacker is still human.
How Infections Occur
Typically, ransomware infections come through phishing (an attempt to obtain sensitive information by masquerading as a trustworthy person or organisation) attacks which cause you to unwittingly download the malicious entity in the form of an attachment purporting to be photos, reports, invoices, resumes or other business and personal communication. When you open the attachment, it will install the Ransomware which will immediately start encrypting data files. Note that Ransomware will also encrypt files in any drives connected to the computer. Websites are also being attacked and you may suffer consequences as an innocent bystander if you visit an infected website where the malware can be downloaded and installed without your knowledge. This is called a Drive-by-Download. Attackers also operate through advertising by injecting infected advertisement into your regular legitimate online-advertising pages.
Once attackers are able to infect a machine, the ransomware will attempt to encrypt anything it deems important to the victim. For websites, this can include webpages, images, and scripts. Once encryption is complete, a message will be displayed to visitors of the webpage stating that the website has been infected with ransomware along with instructions for the web administrator on how to purchase the decryption key and return the website to normal operation
Preventing Successful Ransomware attacks
The Right Mind Set
First things first. You must remove the belief that you cannot fall victim to Ransomware or any other forms of cybercrime. That is the first step towards effective protection. It can affect anybody and everybody so long as you are in possession of or in control of data that is of significant importance. With the wrong mind-set, you are at great risk of temporary or permanent loss of your personal information or your organization’s information. Your loss could be compounded by financial loss from fees payable to professionals in an effort to recover personal files, financial loss due to business disruption and damage to individual or organizational reputation.
Be Vigilant and Stay Up to Date
Secondly, you (and your staff) must at all times remain extra vigilant. You must remain on the lookout for anything suspicious and never click on links or open attachments from unknown sources or in emails that appear to be legitimate but are still suspicious and/or unexpected. If you receive an email from someone you know and regularly communicate with but the mail still looks suspicious (their account may have been compromised), make an effort to contact the individual to confirm that he or she indeed sent you the mail. Ensure email filter/Spam filter settings are enabled to block emails with suspicious attachments. Be sure to scan all downloads before executing. Regularly educate yourself and your staff by updating knowledge because cybercrimes are constantly evolving. The more you understand about them the easier they are to prevent.
Conduct Regular Audits
For enterprises with appreciably sized networks, you should conduct regular vulnerability scanning (conducting an assessment of the weaknesses) of said network, network devices and web applications to identify any potential loopholes exposing you to attacks. You should also conduct penetration testing to assess how to what extent identified vulnerabilities can be exploited by an attacker.
Proper Defensive Tools
Keep operating systems, antivirus, browsers, IDP, IPS and other programs updated because though these tools are useful, they may not be able to stop the most recent versions of malicious software especially in view of the fact that Ransomware software is constantly mutating. Applying updates as soon as they become available is imperative to keeping the bad guys out. Delays, for any reason, may prove costly by leaving your device or network exposed. In many cases, updates are released for the purpose of correcting security flaws in software.
Restrict Access
Employ the principle of ‘Least Privilege’ or ‘Least Authority” (where staff are able to access only the information and resources that are necessary to carry out their duties) to restrict permissions to different cadres of staff based on levels of authority and duties. This will go a long way in preventing unintentional and intentional installation and execution of unauthorized programmes. Apply the principle to all systems and services. Restricting these privileges may prevent malware from running or spreading quickly through the network.
Maintain Back Ups
Consistently back up your systems. This is the most important layer of defence so far as Ransomware is concerned. It is important to deploy a data backup and recovery plan with multiple restore points for all critical information which ensures that system backups are stored in a location inaccessible to the infected device thereby inhibiting the ransomware from encrypting files in the backup locations. You may follow the 3-2-1 rule which requires that you maintain three copies of the data, in two different formats and with one of the copies off-site. If you use an external drive for back up, ensure that it is not always left connected to your computer or to a network. This is because Ransomware can access all such drives and consequently encrypt the files located therein. Storing your files in the cloud is not any different as ransomware can easily attack cloud drives mapped to local machines.
Conclusion
While Nigeria is not currently one of the countries with a high incidence of Ransomware, it will continue to be an increasing security risk to both individuals and enterprises. It is important that you are prepared for any eventuality. Education and awareness creation is crucial and we all must continue to think proactively to reduce the risk of falling victim to a Ransomware attack.
About the Author of this Article
Motunlolu Onabolu qualified as a Barrister and Solicitor of the Supreme Court of Nigeria in 1988 and obtained a Master’s Degree in Business Administration in 1997. He is the Managing Partner of the Law firm of Onabolu & Onabolu.
His Professional experience spans the public sector, private sector and private legal practice. Onabolu has dedicated himself to the practice of the law and has set out to uphold and expound he law to the highest professional and ethical standards by employing the core values of Excellence, Diligence, Innovation and Efficiency against the backdrop of a continuous desire for new knowledge and self-improvement. He possesses a keen bias for Law and Practice as it relates to Internet governance, Cybersecurity and also the Legislature.
He is an unrelenting advocate for Good governance and Social Accountability.
Lolu served as Senior Adviser on Legal and Constitutional matters to the Honourable Speaker, House of Representatives in the 6th National Assembly. Lolu has written various high level strategic documents such FROM IDEA TO LEGISLATION: A Lay Guide to How Our Laws Are Made; and ACCESS TO GOVERNMENT RECORDS– A Quick Guide to the Freedom of Information Act 2011.
He is a partner in Vocal Resources and Partners which is an independent consultancy specializing in Internet Governance and Cybersecurity. He is co-founder of Atarah Kids a faith based Non-for -Profit Organization set up to serve as a platform for older kids to articulate their views and adequately express themselves and to facilitate their emergence as a new generation of citizens committed to the tenets of good governance and Social Accountability.
Onabolu is a member of the Nigeria Bar Association (Section on Legal Practice), Chartered Institute of Arbitrators-Nigeria, Institute of Management Consultants, Chartered Institute of Taxation, Commonwealth Lawyers Association and the Commonwealth Association of Legislative Counsel.
Contact:[email protected]; [email protected]







