Sophos Unveils ITDR Solution to Combat Rising Identity-Based Attacks
…Expands Sophos SecOps Portfolio, Delivering Faster Detection of Identity Risks and Exposure of Compromised Credentials Sophos, a global leader of…
…Expands Sophos SecOps Portfolio, Delivering Faster Detection of Identity Risks and Exposure of Compromised Credentials Sophos, a global leader of…

Technology and Social Media Platforms Continue to Dominate Brand Phishing Attacks, Underscoring the Urgent Need for AI-Driven, Prevention-First Security Check…

Kaspersky has launched ‘Cybersecurity: Entry Level’, a new free online course designed to introduce first- and second-year university students of all…

Cyber threats today are constantly evolving, targeting individuals and organisations alike with ever-increasing and sophisticated tactics. Whether you’re scrolling social…

When it comes to responsible digital parenting, it is hard to draw the line that defines the breach of children’s…

Organisations building trustworthy AI are 60% more likely to double ROI of AI projects, underscoring the high cost of ignoring…

As cyberthreats grow more complex and relentless, Africa’s digital ecosystem is facing a new wave of sophisticated attacks. From AI-driven…
As Apple opened preorders for the new iPhone, Kaspersky detected a spike in scam exploiting the device’s launch hype, with fraudsters…

…Recovery Times Improving with 97% of Victims Recovering Encrypted Data; Ransom Payments Fall Sharply; Staff Burnout and Stress on the…

Nigeria’s digital transformation is happening at full speed, and so is the attention of those who would exploit it. At…

Check Point researchers have uncovered a large-scale active phishing campaign abusing Google Classroom, a platform trusted by millions of students and educators…

Microsoft released the final patches for six newly discovered Windows vulnerabilities identified by Check Point Research, including one rated as…
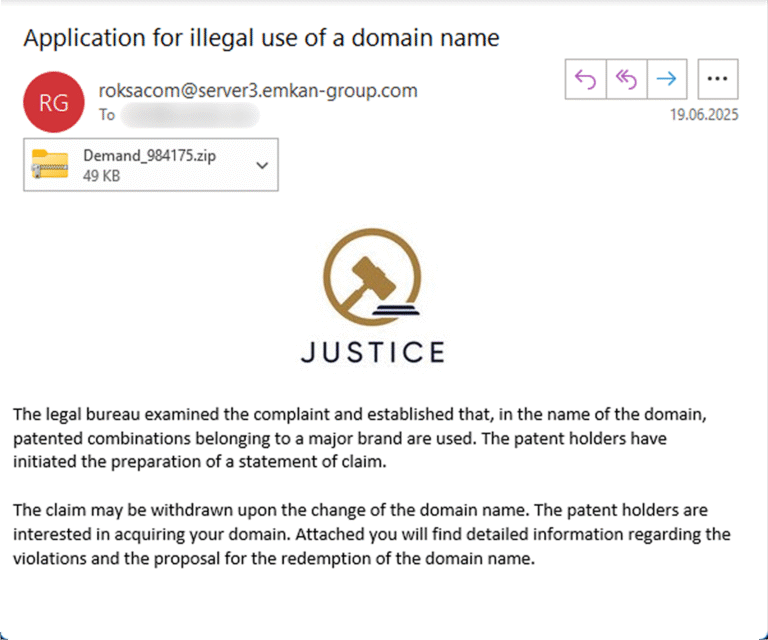
According to Kaspersky Security Network, between October 2024 and July 2025, over 5,000 users — both individuals and organisations —…

The global insurance industry faces a $1.8 trillion protection gap – the difference between insured and uninsured losses across health,…

Kaspersky researchers have discovered a new wave of scam attacks that use Google Forms to target crypto users. Knowing the…

Data is a critical asset to any business, and its protection has become more complex and essential than ever before. And…

…Positioned as a Leader for the 16th Consecutive Time Sophos, a global leader of innovative security solutions for defeating cyberattacks,…

While global attention remains fixed on high-profile cyber incidents in North America and Europe, a quieter crisis is unfolding much…

…Expands Visibility of Internal Exposures within an Organization’s Environment Sophos, a global leader of innovative security solutions for defeating cyberattacks,…

DieNet, a newly emerged hacktivist group, has claimed responsibility for more than 60 distributed denial-of-service (DDoS) attacks in just two…

Cybercriminals are becoming increasingly sophisticated, with SafePay rising as a top ransomware group, while FakeUpdates remains a persistent global threat….

Article written by Samuel Edet, Business Growth Analyst Recently, cybersecurity has become about fostering trust, accelerating innovation, and driving long-term…

West Africa’s distributed denial of service (DDoS) threat landscape was led by Nigeria and Mali, as revealed in NETSCOUT’s recently…

Mart Networks, a leading cybersecurity distributor in Africa and the Middle East, has announced the launch of a dedicated cybersecurity…

…Program Provides MSPs with Exclusive Solution Access, Discounts, Rebates and Training to Deliver Unmatched Cybersecurity Defenses with the Sophos Central…

Massive potential cost to economy if current cyber security measures fail •An organization in Nigeria is being attacked on average…

Eight African countries among the Top 20 most targeted by malware campaigns; education sector remains top target globally Check Point®…

The acceleration of cloud adoption has brought with it new security challenges for organisations to tackle, particularly pertaining to hybrid…

The recent success of the Shanghai Motor Show is a strong indicator of the growth of the Chinese automotive sector,…

New report unveils four key AI-driven cyber threats and how organisations can outsmart attackers in an AI-driven world Check Point…