The Blockchain underlying technology explained
In our previous post, we wrote about a broad overview of what blockchain is and its technicality guide.
Today, I will list and explain the underlying technology of blockchain. There may be a few other more which we may not cover in this post. But our focus is on the main technology found in the blockchain.
The blockchain is a distributed ledger that uses various forms of cryptography to digitally sign blocks of data to ensure the integrity of the data.
We will focus on the two main technologies in a typical blockchain implementation; distributed ledger and cryptography. The different implementation might add to this but this is the basic technology stack for blockchain.
Distributed Ledger
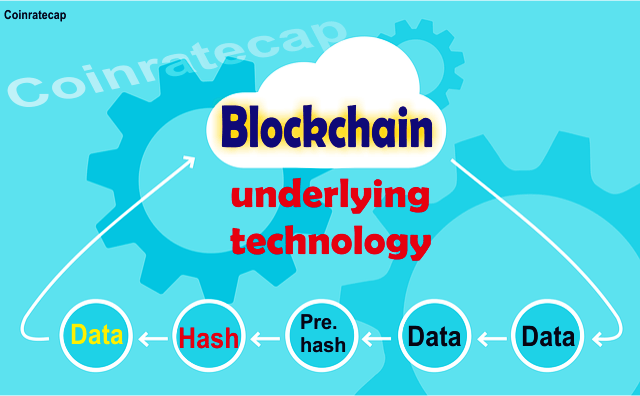
A distributed ledger database is really the core value of a blockchain technology implementation. It is basically storing a series of transactions in a way where the hash or cryptographical signature or the previous transaction is used to encrypt the next transaction.
At the core level, blockchains act like ledgers. For ledgers to function they need to be able to reference people. A blockchain needs to be able to say ‘Kate’s Account sends 1 Bitcoin to Jamal’s Account.’ This is to say, users need some kind of account.
Every user has an account with two parts: a Public Key (often called a Public Address ) and a Private Key (the two variations of the distributed ledger). Think of it as your email account. People send emails to your email address; people send cryptocurrency to your blockchain address. To send an email, you have to use your password to log in; to send cryptocurrency, you have to use your private key to log in. (This is a bit of an oversimplification, just for the purposes of getting the idea down.)
Email address, email account password is the same as saying Public Address, Private Key. These are analogous.
Your email password should never be given to anyone because your password grants complete control over your account. In the same way, your private key should never be given to anyone else.
Don’t worry, no names are involved. Instead, your Public Address and Private Key will both be long, random strings of numbers and letters. This is what protects your identity.
All of the behind the scenes technical legwork is handled by a piece of software called a wallet – you don’t actually have to know any code.
Every transaction that occurred in a blockchain is reviewed by each computer on the network, and each computer has its own copy of the public ledger. The computers check to see that your digital signature is valid and that your address has the necessary funds to complete the transaction. This is referred to as ‘transaction verification’. Once your transaction is verified, individuals called miners come in to do the heavy lifting with fancy, number-crunching computers.
There are variations to distributed ledger technology such as if it is private or public, what type of hash is used, is there a ‘work’ mechanism and what type of peer to peer networking is implemented, but this series of blocks that have a hash-based integrity mechanism is the core of distributed ledger technology.
Cryptography
Cryptography is a process of constructing and analyzing protocols that prevent third parties or the public from decoding private messages. cryptography is used in various aspects of information security like authentication, data confidentiality and data integrity.
There are many types of cryptography. Typically, for the majority of popular blockchain implementations, hashes and public key cryptography are used to ensure distributed ledger integrity. For example, Bitcoin uses SHA-256 to determine the hash cost in blocks before they are created.
Hash cost is a method of slowing down the cryptographical discovery which in Bitcoin provides the award or the actual Bitcoin.
There are often other technologies used in blockchain implementations such as Proof Of Work protocol but this is typically only in public systems. Proof of Stake systems is found in private implementations. The data and the type of hashing vary as well but if you understand the distributed ledger and the cryptography of hashing then you will understand how these variations only go to serve the above-mentioned technologies used in the blockchain.







