Targeted Malware is Proliferating in South Africa, Kenya, and Nigeria

According to the newest danger landscape trends data from internet security firm Kaspersky, South Africa, Kenya, and Nigeria are experiencing tremendous shifts in the landscape.
While traditional, self-propagating malware is declining due to its ineffectiveness and inability to fly under security radars, the region will experience an increase in new cybercrime models in the following year.
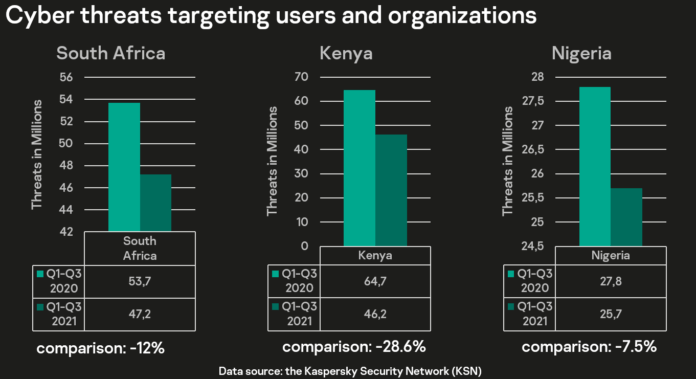
When comparing the overall number of mass cyberattacks in 2021, Kaspersky security experts discovered a 7.5% decline in Nigeria, a 12% fall in South Africa, and an astonishing 28,6% decrease in Kenya.
The reason for such a shift was the introduction and popularization of new cybercrime models in the region, with cybercrime tools becoming more targeted, as well as a long-running trend in which malware creators rely on the human factor rather than the technical advantage of their technologies over security protection. This has accelerated the development of phishing tactics in 2021.
A surge of ‘Anomalous’ spyware infections hit the region in particular.
The typical phishing spyware assault begins with attackers infecting a victim via e-mail with a malicious attachment or a link to a compromised website and concludes with the spyware being downloaded and activated on the victim’s device.
After collecting all essential data, the operator often concludes the job by attempting to exit the compromised system unobserved.
However, in anomalous attacks, the victim’s device serves as both a data source and a tool for spyware dissemination. The virus operators use their access to the victim’s email server to send phishing emails from a real company’s email address.
In this scenario, anomalous malware targets a company’s server in order to steal data from another company and send more phishing emails.
“Anomalous spyware attacks have a huge potential for growth in South Africa, Kenya, and Nigeria in 2022, because, unlike regular spyware, the entry-level for attackers who want to use this tactic is significantly lower – because, rather than paying for their own infrastructure, they abuse and employ the victims’ resources.”
We notice that in the region, cheaper attack methods have always been on the rise, and hackers quickly pick up on new strategies. As a result, Kaspersky recommends that these countries prepare for such attacks in the near future,” says Maria Garnaeva, Senior Security Researcher at Kaspersky ICS CERT team.
However, large-scale attacks are changing rather than disappearing. Garnaeva also reports on large-scale and widespread fake installer efforts, in which bogus pirated software websites give out malware as a service.
The typical strategy is as follows: a user searches for a free version of a widely used legal spyware.
The cybercriminals are providing customers a phony installer by abusing legitimate search engines, resulting in the offering of fraudulent websites first. A few hundred malware samples are downloaded and installed as a result of software installer execution, with the purpose of converting compromised devices into members of the Glupteba botnet.
The entire fake installers campaign and botnet has been quite active in South Africa in 2021 and continues to expand, despite the fact that it is largely unstudied.
“While the Glupteba botnet seems to be a threat for consumers, we are still researching it and keeping an eye on its behaviour, since some distributed malware resembles APT-related samples like Lazarus APT groups and were recently used in the largest DDoS attack in Russia.
It is too early to say it with a high level of confidence, but these factors may suggest that we are now entering the era where APT actors start to use existing malware distribution platforms which makes attribution of such attacks harder and opens a new vector similar to supply chain attacks,” adds Garnaeva