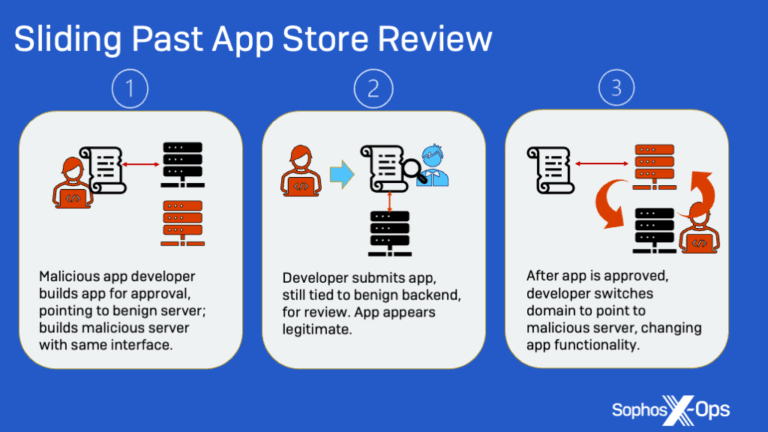
CryptoRom Scammers Add AI Chat Tool, Like ChatGPT, and Fake Hacks on Crypto Accounts to Their Toolset, Sophos Finds
Sophos, a global leader in innovating and delivering cybersecurity as a service, today released new findings on CryptoRom scams—a subset of pig butchering (sh?…