Africa’s Cybersecurity Talent Crisis Is Getting Harder to Ignore
The numbers tell a stark story. A continent of 1.4 billion people, one that is digitizing at a pace few…

The numbers tell a stark story. A continent of 1.4 billion people, one that is digitizing at a pace few…

Nigeria’s banking sector has grown remarkably over the past decade. Mobile money transactions, USSD banking, and digital wallets have pulled…

Kaspersky has detected a new malware for Android devices that it dubbed Keenadu. This malware is distributed in multiple forms…

As digital systems become more interconnected and dependent on invisible technical foundations, new categories of cyber risks are emerging beyond…

Today Monday, February 9th, 2026 is Safer Internet Day, which has always been about protecting people online. In 2026, that mission takes on new…

Check Point’s 2025 Financial Threat Landscape Report, released this week, shows that the financial sector experienced an unprecedented rise in…
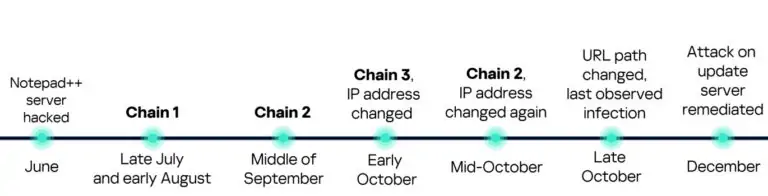
Kaspersky Global Research and Analysis Team researchers have discovered that attackers behind the Notepad++ supply chain compromise targeted a government…

Check Point Software Technologies Ltd. (NASDAQ: CHKP), a pioneer and global leader in cyber security solutions, today released its Cyber Security…

With organisations experiencing an average of 2207 cyber attacks per week according to Check Point’s Threat Intelligence Report, cyber security is…

As global leaders gather for the World Economic Forum (WEF) Annual Meeting this week to discuss “A Spirit of Dialogue,”…

Kaspersky has released Protection beyond detection: Why trust and transparency decide your cybersecurity future, a new whitepaper based on an independent transparency…

For many African startups, speed is survival. Teams race to launch products, acquire users, and prove traction before funding runs…
MENXTT NG has announced that it will begin bundling Bitdefender Antivirus with all laptops sold by the company in 2026,…

As the new year approaches, cybercriminals are once again taking advantage of the holiday atmosphere to target gullible Indian smartphone…

Key Insights AI and automation have made holiday scams smarter and harder to detect. Over 33,500 Christmas-themed phishing emails and…

Sophos, a global leader of innovative security solutions for defeating cyberattacks, has announced its best-ever results in the MITRE ATT&CK…

In today’s digital economy, cybersecurity is no longer just an IT concern, it is fast becoming a strategic business differentiator….

Sophos, a global leader of innovative security solutions for defeating cyberattacks, today announced new findings from the Sophos State of Ransomware…

Sophos, a global leader of innovative security solutions for defeating cyberattacks, today announced the general availability of new integrations that…

Trust alone isn’t a security strategy. That’s the key lesson from new research by Check Point Research, which recently uncovered multiple…

Sophos, a global leader of innovative security solutions for defeating cyberattacks, today released its fifth annual Sophos State of Ransomware in…

Synthetic audio and video generation technologies, known as deepfakes, have reached a critical threshold. Once mostly limited to social media…

NETSCOUT 1H 2025 Threat Intelligence Report shows range of targeted regional industries As the results are analysed from the release…

Meta, as part of its ongoing global anti-scam awareness campaign, has shared the latest trends in scams targeting older adults,…
…Expands Sophos SecOps Portfolio, Delivering Faster Detection of Identity Risks and Exposure of Compromised Credentials Sophos, a global leader of…

Technology and Social Media Platforms Continue to Dominate Brand Phishing Attacks, Underscoring the Urgent Need for AI-Driven, Prevention-First Security Check…

Kaspersky has launched ‘Cybersecurity: Entry Level’, a new free online course designed to introduce first- and second-year university students of all…

Cyber threats today are constantly evolving, targeting individuals and organisations alike with ever-increasing and sophisticated tactics. Whether you’re scrolling social…

When it comes to responsible digital parenting, it is hard to draw the line that defines the breach of children’s…

Organisations building trustworthy AI are 60% more likely to double ROI of AI projects, underscoring the high cost of ignoring…